Fraud Prevention Standards & Anti-fraud Solutions | Mobio Group

While users’ widespread access to apps and media formats across multiple devices and operating systems has offered rich opportunities for mobile advertisers, it has in turn multiplied the number of fraud touchpoints and attacks from potential thieves. In this article, we looked at modern anti-fraud solutions for standards such as App-ads.txt and the mechanisms of both standalone and embedded anti-fraud systems that have become key strategies for creating a safer advertising ecosystem.
Ad fraud represents a significant part (though not all) of a phenomenon that has come to be known as invalidated traffic (IVT) in many markets. In general, it is the fraud of online ad impressions, clicks, conversions or other revenue-generating events (for statistics on the increasing threat of fraud, see our article). A distinction is made between General Invalid Traffic (GIVT) and Sophisticated Invalid Traffic (SIVT):
· GIVT
This is typically automated traffic generated by search engine robots, legitimate bots, proxy servers with traffic coming through virtual private networks (VPNs), and more that does not mimic human behavior. This makes it relatively easy to detect. However, such invalid traffic is not 100% harmless. For example, it can lead to bursts of traffic not caused by real users, which can skew audience measurement data. Such invalid traffic can be detected using standard list filtering or parameter validation.
This is traffic that generates fake views or clicks to generate more revenue. Fraudsters generate SIVT in a variety of ways: domain spoofing, device hijacking, cookie insertion, and the like (we looked at types of fraud in more detail in our article). This type of traffic is difficult to detect because it mimics human behavior and is not conspicuous. Detecting SIVT requires deep analytics and a trusted technology provider with a good track record of operating in an advertising environment.
The problems associated with IVT go beyond losing money in the form of wasted impressions. The impact of such traffic on the number of impressions served affects other metrics as well, including viewability, brand lift and sales. If unchecked, different levels of IVT across campaigns undermine results and make benchmarking and optimization on other metrics irrelevant and nearly impossible.
In response, brands and agencies are using advanced technology to monitor and prevent fraud across all areas of the digital marketplace.

Source: statista
However, huge investments in anti-fraud measures do not serve as a guarantee of 100% protection and complete safety — fraudsters are also perfecting their schemes and using the latest technologies for criminal activities. A high-profile example is the scandal involving the well-known digital threat protection platform HUMAN. The criminal group VASTFLUX managed to forge about 1,700 applications, set up targeting for 120 publishers and run ads on 11 million devices. As a result, over $327 billion dollars spent by advertisers on targeting users interacting with popular mobile apps resulted in over 12 billion fraudulent ad requests per day.
Standards and Programs,
Aimed at Preventing Fraud in Advertising
A number of industry working groups and organizations such as the Interactive Advertising Bureau (IAB), Media Rating Council (MRC), Trustworthy Accountability Group (TAG) accredit specific solutions and vendors to combat ad fraud and issue industry standards and programs designed to protect against fraud and focused primarily on the programmatic advertising sector. So to clean up the online ad supply chain and increase transparency in mobile ads, the IAB’s ads.txt project was developed.
Ads.txt is a text file that publishers can use to authorize those who can sell their ad space digitally. By specifying the original authorized reseller of the publisher’s resources, Ads.txt eliminates domain spoofing and arbitrage, in which impressions are bought, repackaged and resold by a third party at a higher price.
Since mobile apps don’t have a web domain to store a list of authorized sellers, App-ads.txt was created to help apps accept bid requests from ad networks and SSPs listed in the file. Appsflyer states that “proper implementation of app-ads.txt eliminates the need for publishers to worry about losing revenue due to app plagiarism or fake inventory. Instead, they can get their hands on every dollar an advertiser spends on their inventory.” The rollout of app-ads.txt, designed to help advertisers purchase mobile ad space only from legitimate and authorized vendors, is happening at a rapid pace:
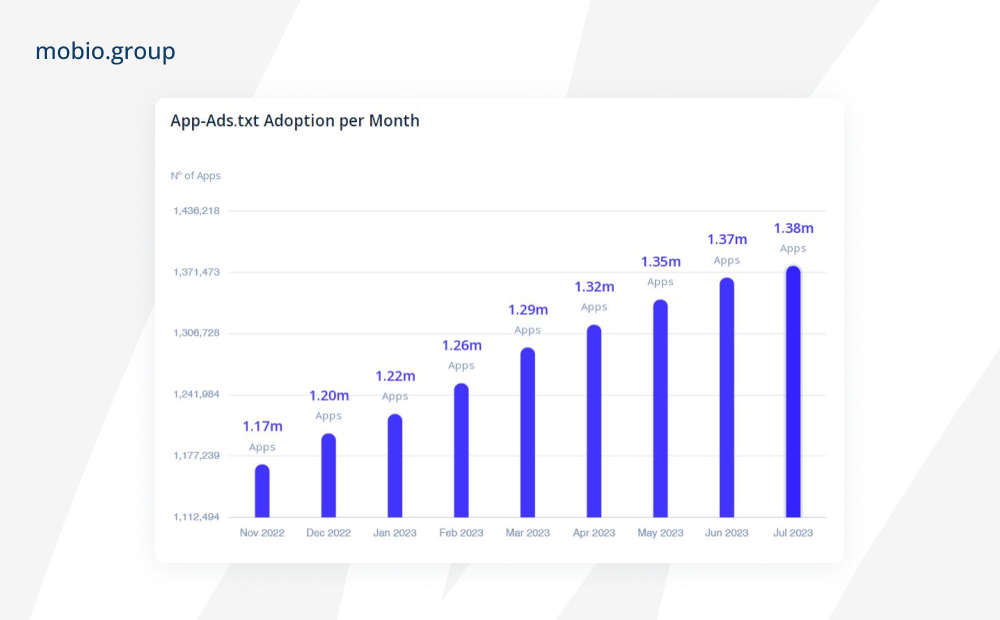
Source: 42matters
The sells.json file listed on an exchange allows advertisers greater transparency into the buying process. It enables verification of ad inventory sources, direct publishers and resellers of traffic on ad tech platforms, SSPs and ad networks is another IAB Tech Lab standard.
Ad insertion and other sophisticated types of fraud also help detect the Ads.cert technical specification, which adds an additional layer of authentication and transparency by cryptographically signing bid requests from publishers.
Anti-fraud Systems
With the current volume of digital interactions, it is unrealistic to manually monitor every transaction for fraud. Connecting anti-fraud systems is becoming an urgent necessity. Virtually all anti-fraud advertising tools and software include basic standard features:
- Data collection
Systems collect various types of data related to mobile transactions, including user behavior, device information, location data, transaction history, and more. This data serves as the basis for identifying deviations from normal patterns. Data collection can occur in real-time or in batch mode.
- Data Storage
The collected data is stored in databases or data warehouses for further processing and analysis. Both relational and NoSQL databases are used to handle large volumes and a variety of data.
- Data pre-processing
The collected data is cleaned, organized and standardized to ensure consistency and accuracy. This step involves normalizing, transforming and filtering the data to make it suitable for analysis.
- Feature Extraction
Relevant features or attributes are extracted from the pre-processed data. These features may include user login times, transaction amounts, geolocation data, device IDs, and more.
- Model training
Machine learning models are trained using historical data that includes both legitimate and fraudulent transactions. These models learn to distinguish between normal and abnormal patterns based on extracted features.
- Anomaly Detection
At runtime, the systems monitor incoming mobile transactions. They compare the observed patterns with the learned models to detect anomalies or outliers.
- Risk Assessment
Detected anomalies are assigned a risk score indicating the likelihood of fraud. This score helps prioritize alerts and responses based on the severity of potential fraud.
- Alert and Response
Depending on the risk score and predefined thresholds, the system takes appropriate action. This may include blocking the transaction, sending alerts to administrators, requiring additional authentication steps, or flagging the transaction for manual review.
- Reporting
A user interface allows administrators to monitor system performance, view alerts, customize rules, and create reports on fraud trends and system performance.
- Feedback loop
Manual checks for flagged transactions help improve system performance, accuracy, and efficiency.
The major anti-fraud systems share a typical architecture:
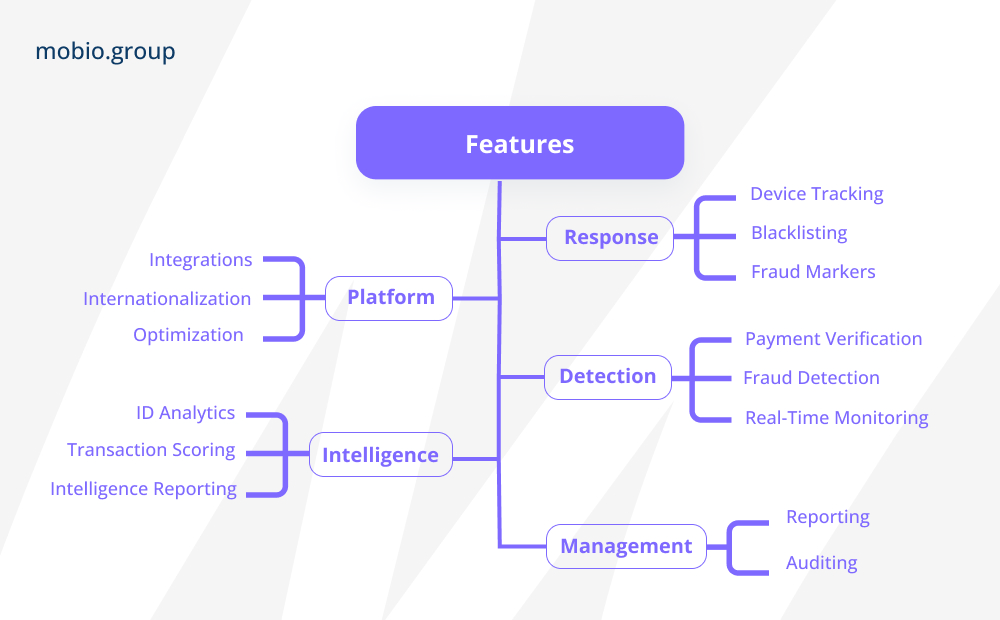
There are two different approaches to implementing fraud detection and prevention mechanisms in different contexts — standalone and embedded anti-fraud systems.
Standalone Anti-fraud Systems
Standalone fraud protection systems refer to specialized and independent software or hardware solutions designed specifically to detect and prevent fraud. These systems operate independently of the underlying applications or processes they are designed to protect.
The key characteristics of standalone anti-fraud systems are:
- independence: systems operate separately from the underlying applications, services or processes they monitor.
- Specialization: services specialize specifically in fraud detection (while embedded systems work in the context of the core application functions).
- flexibility: standalone systems can be integrated with different applications or platforms, making them adaptable to different environments.
- сonsolidation: services provide centralized control and reporting, allowing administrators to manage and track fraud-related activities from a single interface.
- Scalability: standalone systems can scale to handle different volumes of transactions or activities, making them suitable for businesses of different sizes.
Fraudlogix
Online advertising fraud detection platform makes direct, real-time contact with over 1 billion unique devices across 300 million URLs and applications. Identifies over 40 different anomalies that are assigned a weight based on type and severity to identify traffic originating from bots, scripts and hijacked devices (e.g., unmatched browser sessions, geo mismatches, poor device reputation, proxy usage, etc.).
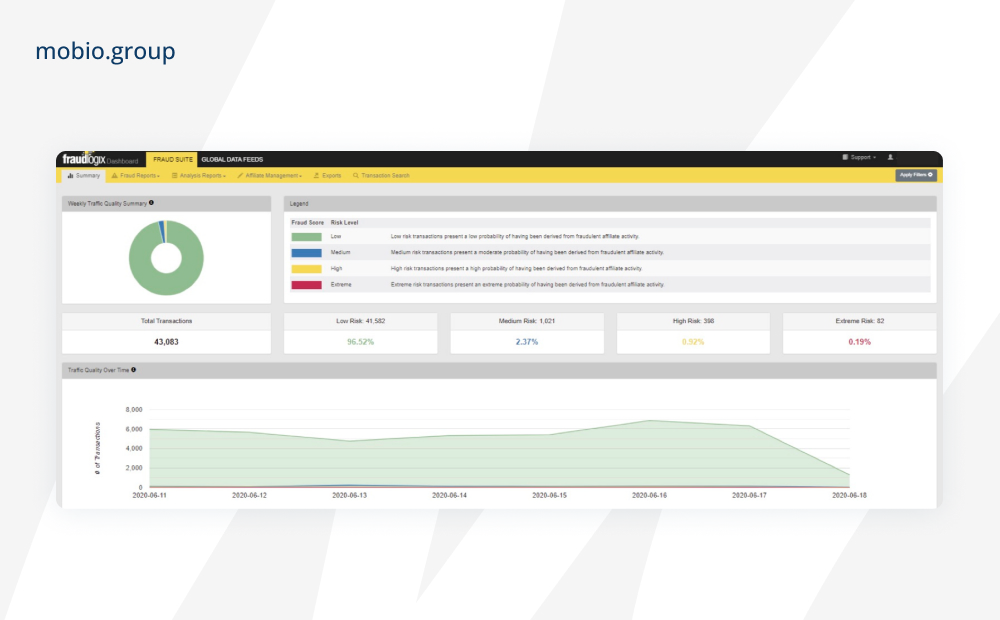
FraudScore
One of the most well-known and highly accurate feature-rich anti-fraud platforms. Detects a wide range of affiliate fraud including ClickSpam, VPN and proxy servers, recurring IP addresses, incentive traffic and more. Depending on the platform and campaign type you’re using, you can choose to integrate Postback, API, Pixel or JStag. All your data from FraudScore can be used in your own business intelligence tools using the Data API.
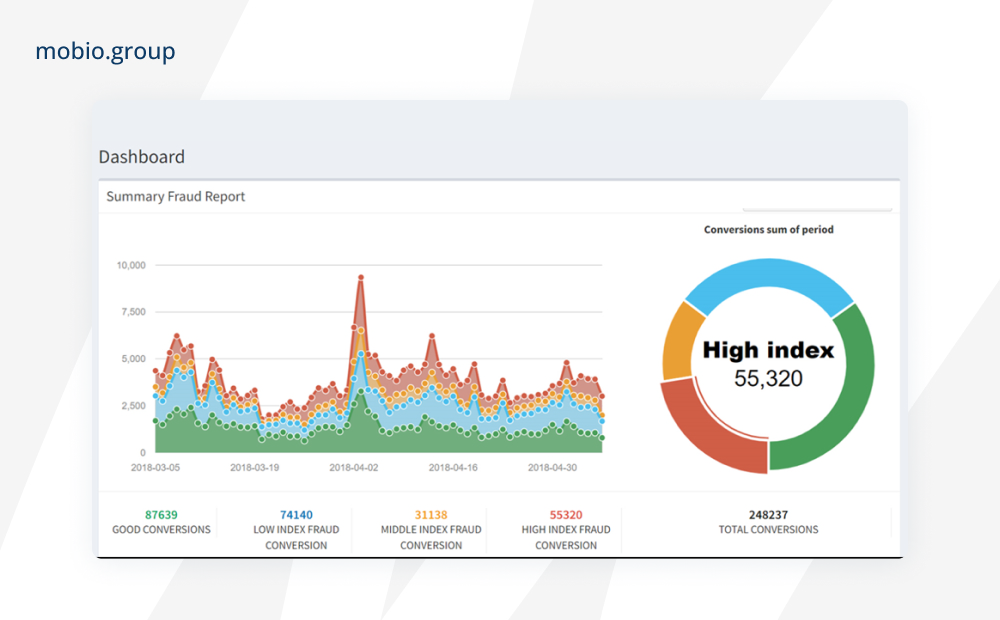
Kount
Fraud management, identity verification and online authentication platform, empowers digital businesses and online merchants to verify e-commerce transactions. Used primarily to determine whether a transaction is fraudulent or not, to reduce the overall risk of chargebacks and reduce overall customer support operations.
Other fraud detection software vendors include ComplyAdvantage, Featurespace, Feedzai, Unit21, Sardine, and Hawk:AI.
Integrated Anti-fraud Services
Embedded fraud protection systems integrate directly into existing applications, platforms or processes, tightly woven into their structure and functions. This integration provides a seamless user experience, as anti-fraud measures are invisible to end users and take place behind the scenes.
Key characteristics of embedded anti-fraud systems:
- integration: services are embedded into existing applications or systems, working closely with their core functions.
- Seamlessness: embedded systems operate transparently to users because they are part of the workflow of the underlying application.
- Context: systems leverage application-specific data and user behavior patterns to improve fraud detection accuracy.
- Simplicity: the setup and maintenance of embedded systems is often simplified because they are closely aligned with the core application.
- real-time response: integrated services can respond more quickly to fraud because they are part of the same operational context as the core application.
- maintenance: integrated systems have easier maintenance because of their integration, while standalone systems may require specialized management.
Major built-in anti-fraud systems (with G2 rating):
AppsFlyer
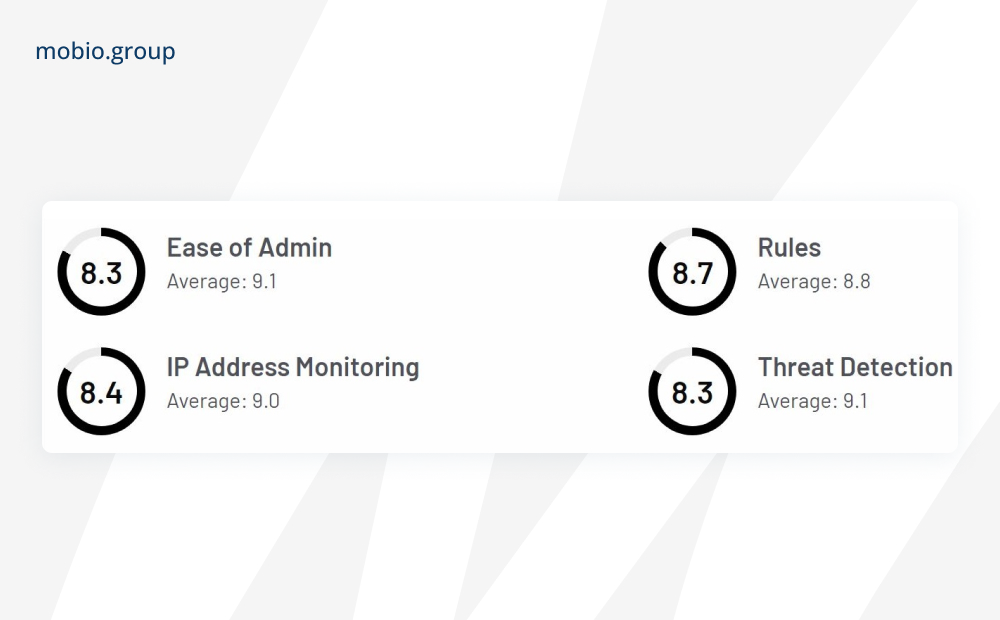
Widely used platform with a strong focus on mobile attribution and anti-fraud capabilities. Integrates with various ad networks and provides real-time fraud protection. AppsFlyer uses proprietary algorithms and machine learning to detect and filter fraudulent activities such as fake installs, click spam and device emulators. The service analyzes patterns and inconsistencies in user behavior to detect anomalies.
Adjust
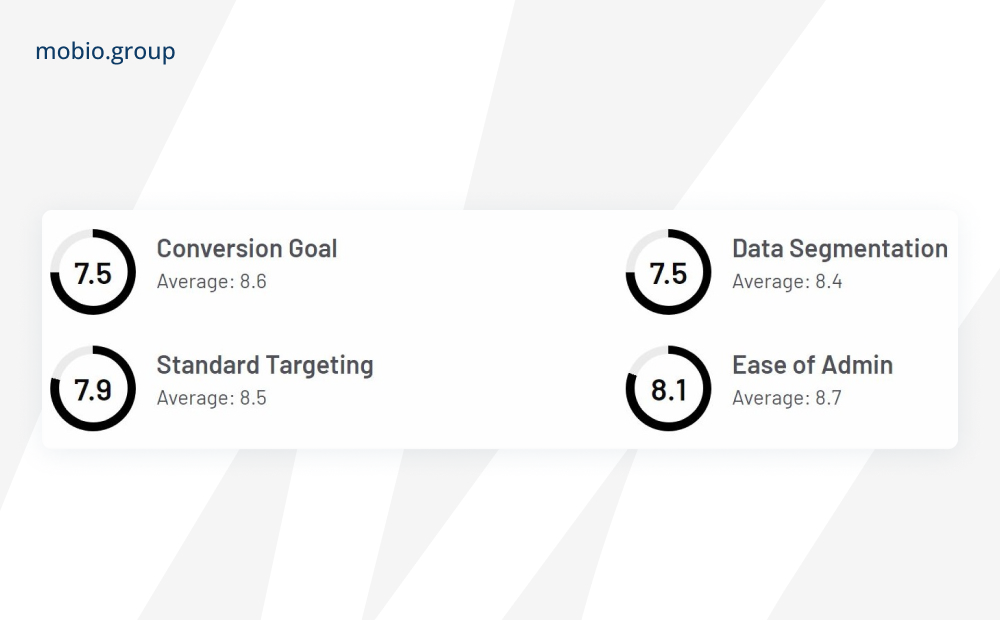
The service is known for its fraud prevention features that complement its mobile measurement and attribution services. Offers detailed reporting and customizable anti-fraud rules, and uses real-time and anomaly detection algorithms to identify suspicious activity.
CHEQ Paradome
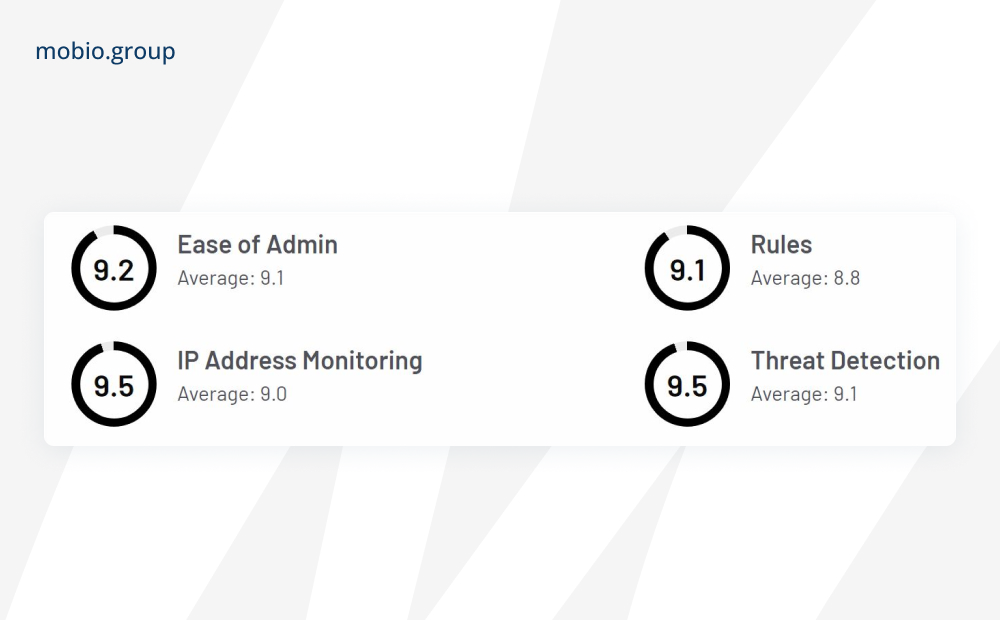
Specializes in ad verification and brand safety by preventing fraudulent ad placements, especially in programmatic advertising, using AI-based algorithms to analyze engagement patterns, user behavior, and contextual information.
fraud0
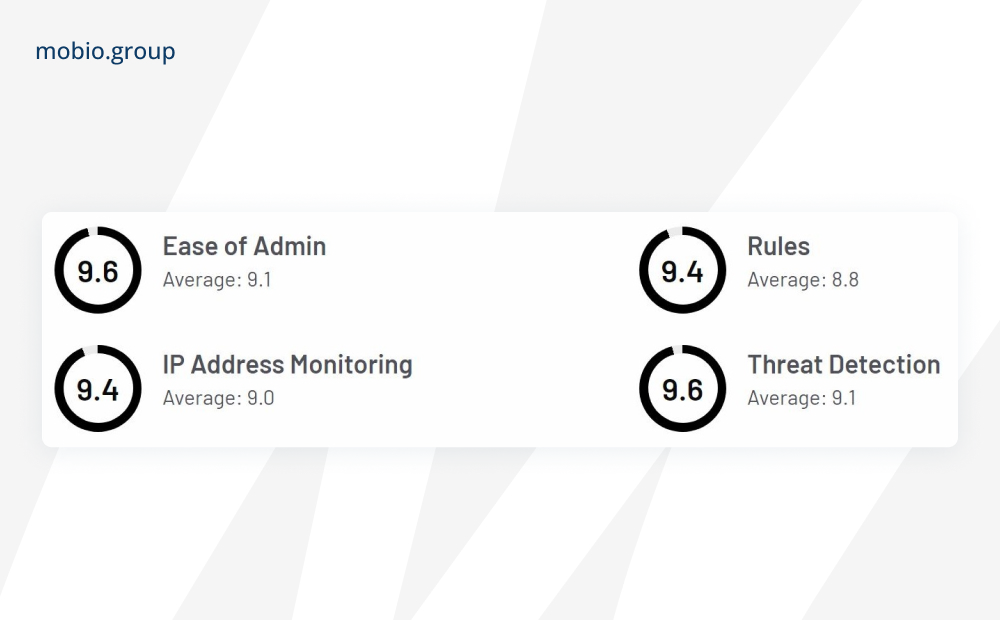
The system minimizes fake traffic automatically in real time with negative audience groups on all channels such as Google Ads, Facebook, Instagram, TikTok, LinkedIn.
Traffic Guard
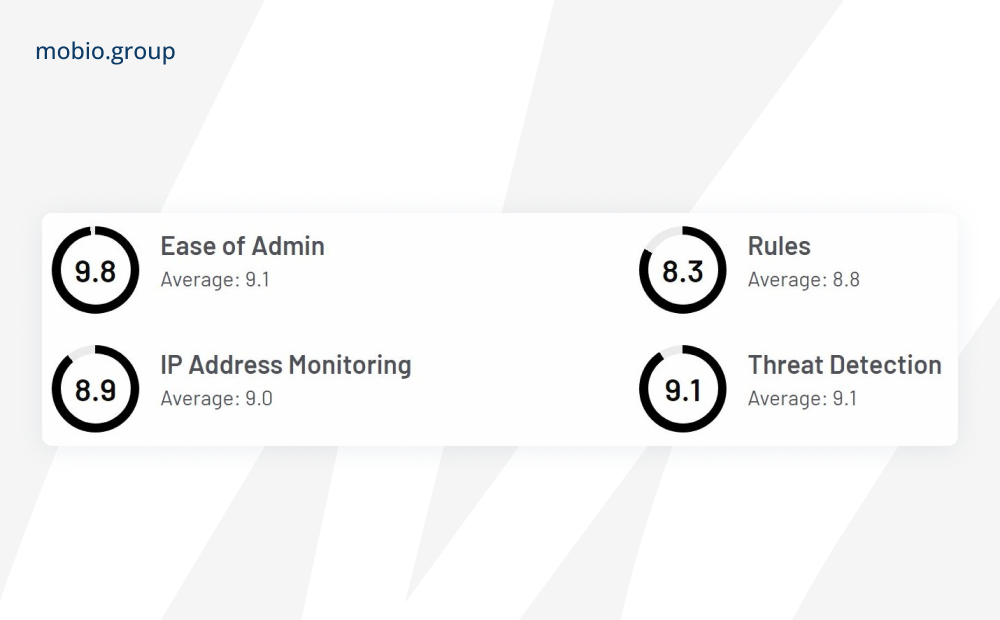
The service is designed to prevent invalid clicks and impressions in digital advertising campaigns across multiple platforms, uses machine learning to analyze traffic patterns, click behavior and conversion data.
Singular
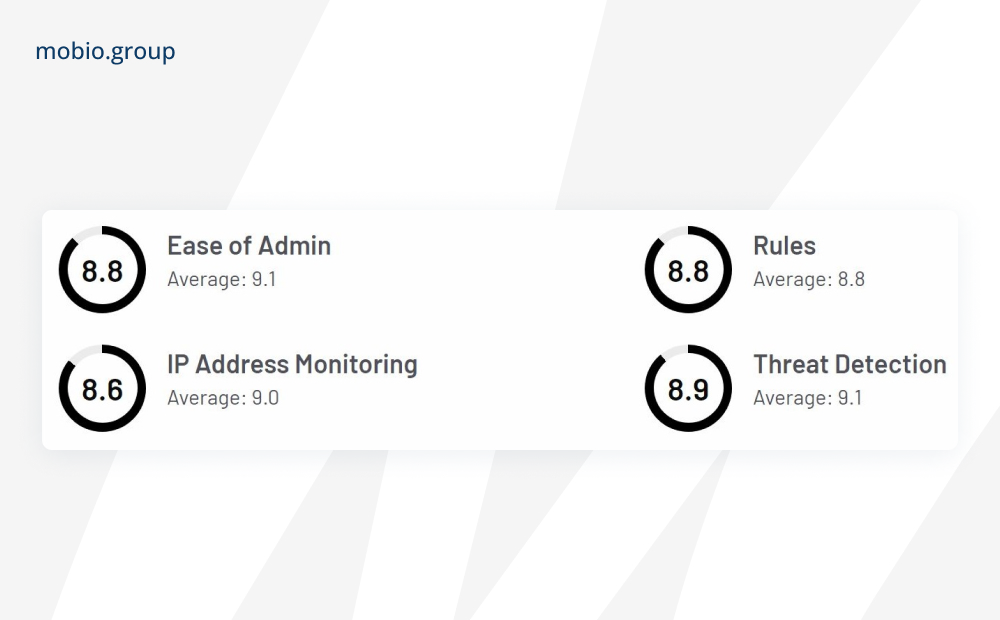
Provides comprehensive mobile attribution, analytics and anti-fraud capabilities in a single platform. Singular Fraud Prevention Suite uses machine learning to identify anomalies and patterns, including attribution fraud and fake installs.
Lunio
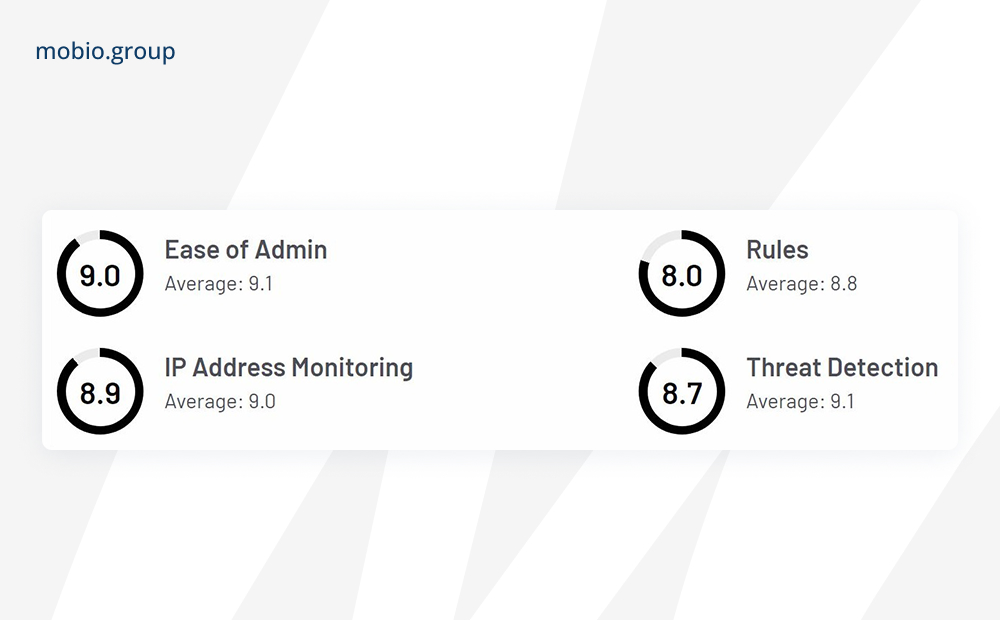
The system offers real-time fraud detection to protect app installations, in-app events, and marketing campaigns from fraudulent activity, using AI-based algorithms to analyze a variety of data including device attributes, user behavior, and user interactions.
When dealing with fraud, we do not use a specific anti-fraud system. There are several reasons for this.
Firstly, we cooperate with a number of premium in-app sources with specific traffic, which some anti-fraud tools regard as suspicious, while in fact, it is clean, not fraud.
Secondly, various third-party anti-fraud systems work according to different principles, using different methods of traffic evaluation. This fact does not allow us to apply them simultaneously to offers, the specifics of which differ significantly. In addition, some MMP anti-fraud systems do not track view traffic, making them vulnerable to some types of fraud.
Thirdly, our long-term experience of working with in-app channels shows that the most correct, workable, and complete approach to solving the problem of fraud traffic is manual analysis and subsequent optimization. Therefore, along with traffic assessment within the framework of the client’s anti-fraud system (if there is such a system), we also assess traffic from raw uploads, analyzing a variety of different metrics. For this purpose, we have analysts in our team, some of whom are primarily involved in the analysis and optimization of fraud. This solution allows us to analyze and optimize the traffic provided for our clients in the most comprehensive and truly high-quality way possible.
Alexandr Igonin, Affiliate Team Lead, Mobio Group
The rise of mobile ads has given huge advantages to companies looking to connect with their target audience on mobile platforms. The convenience and accessibility of mobile devices allow advertisers to engage users wherever they are. However, as opportunities expand, so do new fraudulent tactics that cause quite the damage to all sides of the advertising process.
From solutions that specialize in fraud detection to easily integrated services that complement existing platforms, the concept of fraud prevention is coming to the forefront in the search for comprehensive protection. Fighting fraud in mobile ads requires a collective effort from advertisers, publishers, platforms and technology providers.
Our Mobio Group team keeps a close eye on emerging fraud tactics and utilizes the most advanced technologies to protect our partners. While there is no 100% protection against fraud, together we can create an environment where fraud risks are minimized.