Security and Counteraction to Mobile Fraud: Mobio Group Research

The convenience and accessibility of mobile devices allow advertisers to reach users wherever they are. However, as advertising opportunities expand, new fraudulent tactics are emerging that cause tangible harm to all sides of the advertising process. Mobile fraud is a serious problem that requires the attention of advertisers and marketers, as well as ad networks and publishers, as fraudsters affect all parties-partners of the digital market.
Statistics of Fraud Increase
According to a report by Appsflyer, the volume of mobile fraud has increased dramatically to $5.4 billion by the beginning of 2023. Compared to the same period last year, January 2023 showed a 76% increase in install fraud on iOS and a 154% increase in post attribution fraud on Android. This jump was fueled by improved fraudulent tactics, the release of iOS 14.5, which diverted attention away from the issue of fraud, and limited advertising budgets forcing companies to choose cheaper, insecure ad networks. Improved fraud detection systems have also led to an increase in detection.
The financial, shopping and casino sectors accounted for more than 75% of all fraud incidents, with the financial sector accounting for $2.6 billion. Casinos, which offer high CPI payouts, experienced an increase in fraud, reaching $1.2 billion. In the shopping category, the amount at risk was $406 million with iOS fraud growing 210% over 2022. Gaming apps proved to be more resistant to fraud, and their share compared to non-gaming apps was negligible.
If we analyze the top markets, Android fraud was high in Mexico (34%), Vietnam (21%), India (15%), Russia (11%) and, surprisingly, the UK (21%). In the case of iOS, Russia showed 18%, India 20%, Mexico 19%, Vietnam 28% and the UK 23%. Despite the advanced technological environment, the US had an iOS fraud rate of 8.8% and Australia 11.3%.
Scammers vs. Users
Hackers use a variety of tactics and methods to defraud mobile users. According to FraudWatch International, it is not uncommon to see several hundred iterations of the same fake mobile apps. The main fraudulent activities against mobile users are:
- Phishing — leakage of sensitive information
- Stealth Malware — fraudulent activities ranging from identity theft to tacit subscription to premium services via malware
- The placebo — user payment for downloading a fake app
- Apps packed with Adware — forced display of advertisements
- APP scams — online payment scams.
Users suffer huge financial losses due to fraudulent transactions. This is prompting regulators to retaliate, such as the UK government’s initiative to require app owners to indemnify customers.
Scammers vs. Stores
The simplification of the app verification process on platforms like Google Play and the App Store, designed to speed up the release of apps, has unwittingly provided fraudsters with a more convenient environment. However, the Stores continue to fight the fight against fraud.
The App Store claims to have deleted 282 million fraudulent accounts, 428K developer accounts and blocked 3.9 million stolen credit cards and fraudulent transactions worth over $2 billion in 2022, rejected 1.7 million apps, of which 153K were copycat or spam apps and 29K contained hidden or undocumented features.
Google Play Store has been independently verified since 2022 as part of the Mobile App Security Assessment (MASA) of the App Protection Alliance. MASVS compliance is indicated by an icon in the relevant security section of the app’s data.
Scammers vs. Apps and Mobile Advertising
There are many variations of mobile fraud, but they all have the same goal — to profit from attribution and artificially inflate paid actions (clicks, impressions and conversions).
Attribution hijacking and fake installs drain the budgets of advertisers, ad networks and publishers alike. The damage caused by fraud goes beyond financial losses. According to Statista data, fraud is one of the top reasons advertisers downgrade or suspend their advertising partners.
In order to monitor in-app misconduct, control the course of an advertising campaign, and resist the actions of fraudsters, you need to be aware of the ways in which they cause financial and reputational damage.
Types of Fraud in Mobile Advertising
Click farms and bots are primarily used for mobile advertising fraud:
☑ Click Farms (Device Farms) are physical locations where low-paid workers or automated devices perform fraudulent digital conversions, clicks, installs and attribution by manipulating IP addresses using VPN software and proxy servers.
☑ Bots refer to standalone software designed to perform specific tasks on the network. In mobile fraud, bots can operate from genuine mobile devices or servers, impersonating real users and performing ad clicks, app installs, and unauthorized actions within apps. Server bots use emulators to reproduce the functions of mobile devices. In mobile, bots account for more than 70% of fraud.
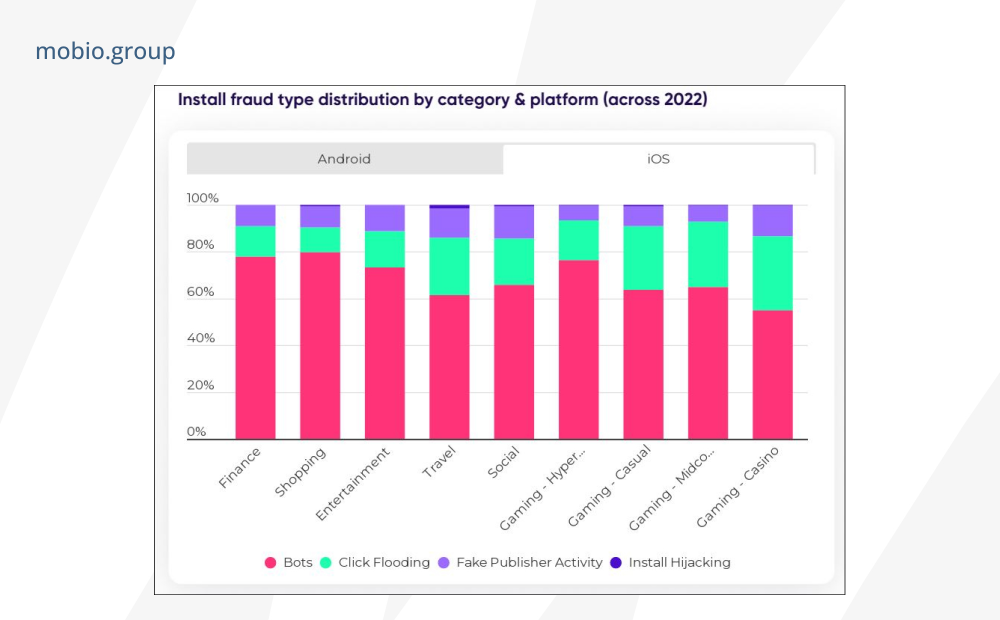
The main types of mobile fraud:
- Click Fraud
- Install Fraud
- Attribution Fraud and SDK Tampering.
- Display Ad Fraud (display ad fraud).
Let’s look at each of the types of fraud in more detail. Some fraud methods can fall into more than one category because they involve different fraudulent activities.
CLICK FRAUD
This type of fraud involves the deliberate act of creating fake clicks in order to increase the scammers’ revenue and deplete campaigns’ advertising budgets in pay per click (CPC, CPI and so on). Common methods of click fraud include:
- Click Injection: a click simulation is run before the app is fully installed to attribute the click to a fraudulent source. Most often, dormant “junk apps” are used.
- Click Hijacking: focuses on intercepting legitimate clicks and reporting false clicks to capture attribution. Most often utilizes malware covertly embedded in apps.
- Click redirection (Auto redirects): manipulates user interaction with clicks by redirecting them to unintended destinations. Achieved through the use of malicious scripts or code.
- Click flooding: manipulates attribution models to artificially inflate the number of clicks.
- Duplicate IP: using bots or a network of devices to simulate more clicks and actions purportedly from different users.
INSTALL FRAUD
Install Fraud refers to actions designed to artificially increase the number of installed applications using Device Farms and emulators. Install Fraud techniques include:
- Device ID reset fraud: resetting or changing device IDs to create the illusion of multiple installations from different devices
- App Spoofing: creating fake versions of popular apps.
ATTRIBUTION FRAUD AND SDK TAMPERING
In addition to Click Injection, Click hijacking and Click flooding, SDK scams are common for attribution data distortion:
- SDK Hacking: spoofing mobile app software development kits (SDKs) to serve unauthorized ads.
- SDK Spoofing: a fake SDK creates fake events and data that appear genuine to attribution systems.
DISPLAY AD FRAUD
This is a form of fraud in mobile in which the ad placement and display process is used to create illegal ad impressions or clicks.
- Ad Stacking: multiple ads are placed on top of each other in the ad placement area of a mobile app, with only the top ad visible to users, and a click or impression is registered for each ad in the stack, forcing advertisers to pay for fake impressions and clicks.
- Ad Injection: the unauthorized insertion of ads on top of legitimate content without the publisher’s consent.
- Pixel Stuffing: placing fake ads invisible to users using iframes.
CPI/CPA FRAUD
Initially, advertisers paid per app install on a CPI model, but fraudsters began using click fraud tactics. To counter this, advertisers switched to pay-per-action (CPA) campaigns, emphasizing in-app events and user engagement. CPA campaigns were expected to discourage fraud and attract higher quality users because advertisers only pay for real results, actions, or installs.
However, attackers have adapted by introducing fake apps and bots into CPA, especially gaming apps.
Payouts for specific actions are higher in the CPA model, which is what attracts fraudsters. At the same time, the activity of fraud in CPI campaigns is still not decreasing: as of February 2023, annual losses from fraud in mobile applications, including CPI fraud, were estimated at $2.05 billion in the European market and $1.2 billion in North America (according to Statista).
Whistleblowing Techniques and Defense Against Fraud
A number of analysis techniques are used to detect and prevent advertising fraud, depending on the time of analysis and the specific stage of the advertising process.
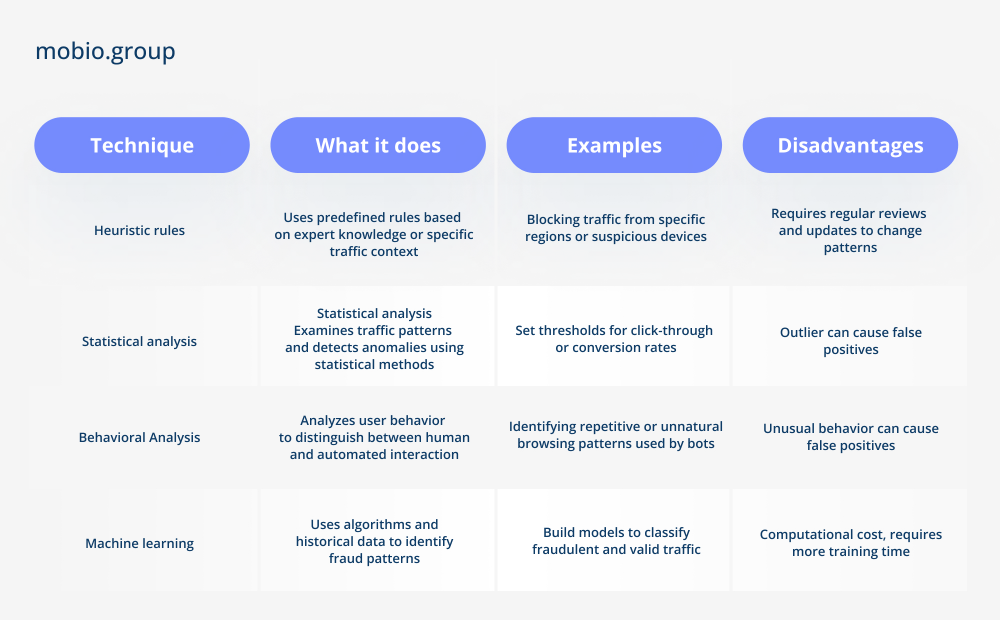
The combination of the above methods helps to detect and prevent fraud, including traffic theft, fake installs, DDoS attacks, and fraudulent payments, through specific metrics and indicators:
☑ Click Metrics. Identify simultaneous clicks on ads from different apps, short installs (CTIT less than 10 seconds), long installs (CTIT 24 hours or more), sudden spikes in clicks, and abnormally low conversion rates.
☑ Hardware Metrics. Detect devices with deviations from expected parameters (incompatible OS versions or screen sizes), track changes in hardware properties between launches, and identify devices with unauthorized access (Root/Jailbreak).
☑ Behavioral metrics. Detect instances of non-startup installation, abnormal duration or suspicious session frequency, hyperactivity or lack of user activity in the application.
☑ Unusual impression surge. Detect abnormal or unexpected increases in the number or frequency of ad impressions.
☑ IP address indicators. Track traffic from untargeted locations or inactive areas.
Anti-Fraud systems that use huge amounts of data, complex algorithms, dynamic tools and machine learning techniques to analyze metrics, statistical and behavioral analysis serve as a comprehensive solution for fraud protection. The main modes of protection are:
- Real-time blocking. When a fraudulent setup is detected, its attribution is immediately blocked, preventing further engagement and attribution of any subsequent internal events from the same user.
- Post-attribution fraud detection. Systems (such as AppsFlyer’s Protect360) continuously monitor installations and internal application events for several days (up to 8) after attribution.
The major anti-fraud systems share a common typical architecture:
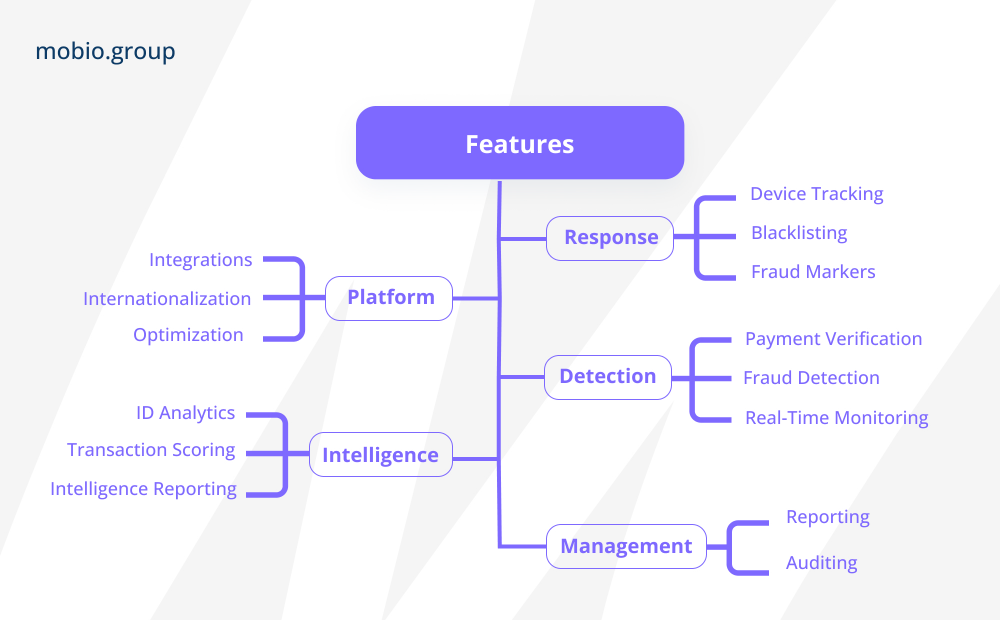
There are two different approaches to implementing fraud detection and prevention mechanisms in different contexts:
- Stand-alone anti-fraud systems that operate independently of the underlying applications or processes they are designed to protect: Fraudlogix, FraudScore, Kount, ComplyAdvantage, Featurespace, Feedzai, Unit21, Sardine, Hawk:AI.
- Embedded anti-fraud systems that are integrated directly into existing applications, platforms or processes and tightly woven into their structure and functions: AppsFlyer, Adjust, CHEQ Paradome, fraud0, Traffic Guard, Singular, Lunio.
When choosing an anti-fraud system, you should keep in mind that these services do not guarantee 100% anti-fraud protection, and scammers are improving their tactics.
The issue of fraud is indeed extremely relevant in in-app advertising. Unscrupulous publishers continuously develop new ways to circumvent anti-fraud systems.
This situation occurred this year with the rise of SDK fraud, which is still not detected by, for example, the widely used anti-fraud system Protect360. Such traffic appears completely “clean” classic fraud metrics are within normal ranges, and anti-fraud tools label it as genuine, non-fraudulent traffic. However, in reality, the intended actions are simulated, and no real revenue is generated for clients. This type of fraud is often found in a significant quantity in CPA (Cost Per Action) offers, typically on Android.
The most effective approach to prevent such traffic is to use a CRM system as a verification tool. We recommend that our clients pay attention to the proper setup of the CRM system and its integration with MMP. In the vast majority of cases, such a partnership system helps protect against SDK fraud and prevents the wastage of the advertising budget on fake traffic that does not generate real revenue.
Alexandr Igonin, Affiliate Team Lead, Mobio Group
The Main Techniques of Anti-fraud and Measures to Combat them Anti-fraud Systems
➲ DeviceID reset scam
Fraudsters: continually reset DeviceID on the same device to generate a large number of fraudulent installations.
Fraud Software: detects an abnormal number of new devices and places their supply sources on the banned list accordingly.
➲ Customization hijacking
Fraudsters: embed malware on mobile devices that sends a notification when an app is downloaded. They intercept click attribution and claim undeserved credit.
Fraud Software: blocks attributed clicks with a very short CTIT defined by server-side APIs such as the Google Play API.
➲ Clickjacking
Fraudsters: malware identifies a click on an installation attribution link and instantly sends another click, which is favored if it is attributed.
Fraud Software: blocks attributed clicks that occur a very short time after other clicks on the same device and application.
➲ Click Flooding
Fraudsters: send out large numbers of fake clicks to ensure the last click before installation.
Fraud Software: blocks clicks received using site IDs with low conversion rates and long CTIT.
➲ Behavioral Anomalies
Fraudsters: perform inconsistent and unusual behaviors after installation to fool fraud protection systems.
Fraud Software: detects “non-human” behavior in near real-time and blocks it at the source. Behaviors are tracked and recognized at multiple levels such as application, region, media source and publisher.
➲ Lists of banned IP addresses
Fraudsters: use click farms that can be identified by their IP addresses over time.
Fraud Software: IP addresses suspected of being involved in fraud are blacklisted daily based on the most recent data from a third-party provider.
➲ SDK authentication
Fraudsters: send spoofed SDK messages to mimic the actions of valuable users.
Fraud Software: the Fraud Protection System uses a proprietary hashing protocol to encrypt messages between the SDK and web services, providing protection against spoofed messages.
However, despite the use of the most advanced technologies, anti-fraud systems and even their combinations do not guarantee absolute anti-fraud protection and to date cannot yet compete with the meticulous and labile “manual” human analysis.
When dealing with fraud, we do not use a specific anti-fraud system. There are several reasons for this.
Firstly, we cooperate with a number of premium in-app sources with specific traffic, which some anti-fraud tools regard as suspicious, while in fact, it is clean, not fraud.
Secondly, various third-party anti-fraud systems work according to different principles, using different methods of traffic evaluation. This fact does not allow us to apply them simultaneously to offers, the specifics of which differ significantly. In addition, some MMP anti-fraud systems do not track view traffic, making them vulnerable to some types of fraud.
Thirdly, our long-term experience of working with in-app channels shows that the most correct, workable, and complete approach to solving the problem of fraud traffic is manual analysis and subsequent optimization. Therefore, along with traffic assessment within the framework of the client’s anti-fraud system (if there is such a system), we also assess traffic from raw uploads, analyzing a variety of different metrics. For this purpose, we have analysts in our team, some of whom are primarily involved in the analysis and optimization of fraud. This solution allows us to analyze and optimize the traffic provided for our clients in the most comprehensive and truly high-quality way possible.
Alexandr Igonin, Affiliate Team Lead, Mobio Group
Despite the constant emergence of new protection tools, fraud in mobile advertising is not only not decreasing, but also continues to grow. To avoid losing their budget due to fraudulent actions, advertisers need to take a thoughtful and balanced approach to choosing a partner to promote their mobile application and the way to protect their advertising campaign from fraud.
Today, the most optimal solution is a combination of anti-fraud systems and “manual” monitoring by experienced specialists. The dual methodology, which includes automation and human professionalism, is quite effective, provided that all changes and innovations in both protection technologies and new ways of fraud are constantly monitored and taken into account.
Following Apple’s Privacy Policy and the ban on IDFA collection, Google’s Privacy Sandbox and a similar ban on GAID collection will follow in the near future. It is quite possible that this will create a favorable environment for the development of new fraudulent schemes in digital and online advertising, which will be an even more serious blow to the advertising market than before, against the background of already changed principles of work. How quickly anti-fraud systems will be able to adapt to the changes is a rhetorical question. In this regard, the availability of direct analytical anti-fraud consulting will become more relevant than ever for advertisers, and advertising agencies, especially those managing advertising campaigns, should definitely think about strengthening anti-fraud analytics to remain competitive in the market.
Anton Afanasyev, Digital Director, Mobio Group
In the advertising business, you can’t learn one thing and keep doing it all the time, because stopping is regression. Mobio Group team is constantly learning, developing and adapting to changing market conditions, striving to maximize the protection of our clients’ and partners’ advertising campaigns and earn their trust.