Protecting Mobile Ads: Fraud Detection and Anti-fraud Measures | Mobio Group

In the advertising ecosystem, all stakeholders are increasingly facing budget depletion as mobile ads fraud continues to skyrocket. In our previous articles, we took a detailed look at the statistics of increasing fraud and types of fraud in mobile ads. In this article, Mobio Group will break down the different methods of analyzing fraud, anti-fraud measures, detection rates, and look at what defenses are at the core of anti-fraud systems to ensure a safe advertising environment.
Based on its research, the ANA (Association of Nationwide Advertisers) has found that mobile banners have become one of the most cost-effective advertising options, attracting advertisers because of their affordability and potential to reach a wide audience.

However, while advertisers use the profitability of mobile ads to maximize their marketing revenues, fraudsters don’t miss the opportunity to resort to deceptive practices and siphon off advertising budgets. As a result, mobile fraud has increased significantly in recent years (see our series of articles). The growth rate of app install fraud in the second half of 2022 compared to the average fraud rate for the first 6 months was 40% for iOS and 46% for Android. At the same time, bots account for the bulk of online traffic fraud.
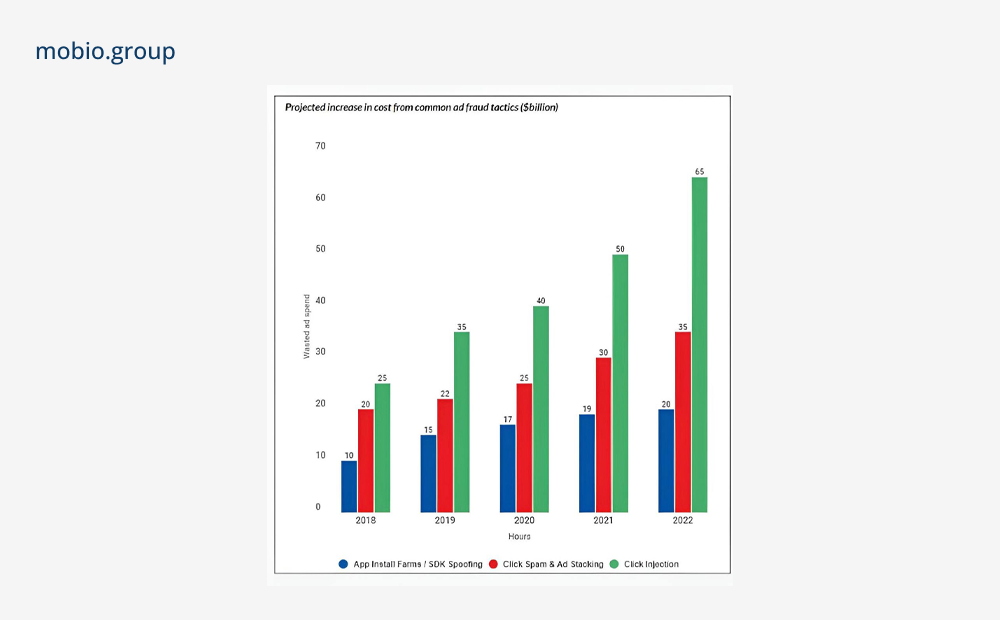
Source: TrafficGuard
Methods of Analysis
Detecting and preventing ad fraud is critical for marketers and advertisers, ad networks and publishers alike. A number of techniques are used to combat malicious ad fraud, depending on the time of analysis and the specific stage of the advertising process.
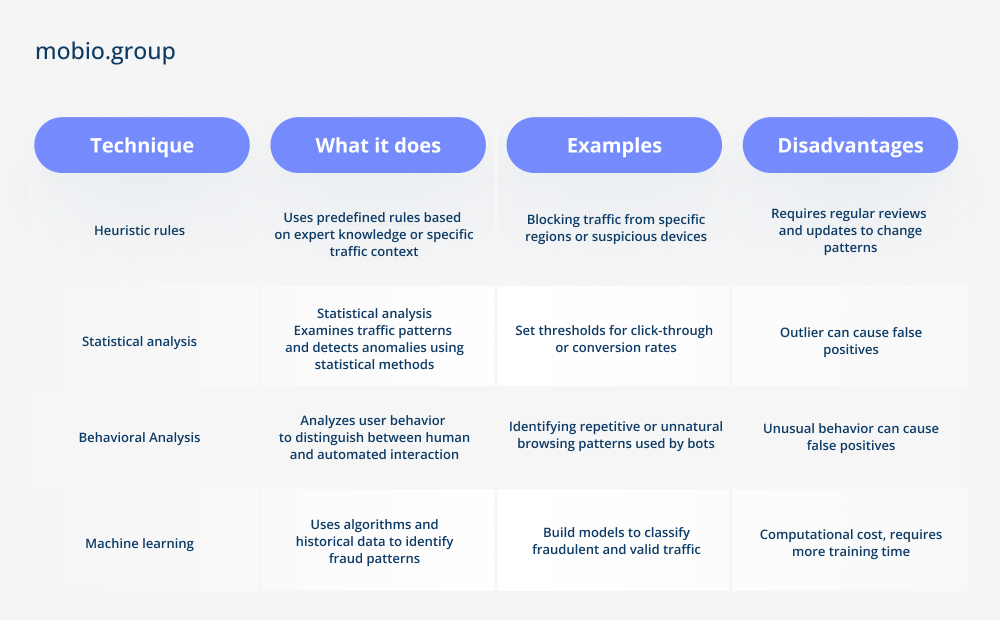
Discovery Metrics
A combination of the above methods are used to detect and prevent fraudulent activity. With this in mind, it is critical to understand the specific metrics and indicators that help detect and measure the presence of ad fraud, including traffic theft, fake installs, DDoS attacks, and fraudulent payments, which place a financial and reputational burden on app owners and advertisers.
Click Metrics:
- Cross-App Clicks: detecting simultaneous clicks on banner ads from different applications, signaling potential fraudulent activity.
- Short installs (CTIT less than 10 seconds) or long installs (CTIT 24 hours or more): detecting devices with unusually short or abnormally long attribution windows (the interval between click/advertisement display and app installation).
- Sudden bursts of clicks: observing a burst of clicks over a short period of time, especially from the same IP address.
- Low CR: tracking the number of devices attracted by ad campaigns with abnormally low conversion rates.
Hardware Metrics:
- Virtual Devices: detect devices with deviations from expected parameters, such as incompatible OS versions or screen sizes, suggesting the presence of emulators or bots.
- Suspicious Devices: tracking changes in hardware properties between runs that may indicate fraudulent activity or device manipulation.
- Root/Jailbreak detection: detect devices with unauthorized access.
Behavioral Metrics:
- Abnormal session duration: tracking unusually long or short session duration, revealing abnormal user behavior.
- Suspicious session frequency.
- Lack of activity: flagging devices with minimal or no user participation, suggesting rogue setups or inactive users.
- Hyperactive installations: detecting devices that exhibit excessive or abnormal installation activity.
- Non-startup installs: detecting instances where users do not interact with the app after installation, which may indicate fraudulent installs or bot activity.
Other indicators:
- Unusual impression surge: an abnormal or unexpected increase in the number of impressions or frequency of ad impressions.
- Abnormal IP addresses: tracking traffic from untargeted locations or inactive areas.
Anti-fraud Systems

To combat fraud in the digital environment, anti-fraud systems provide an intelligent and comprehensive solution, detecting and preventing various types of fraud and offering a range of protective measures to ensure a safe advertising environment.
Functioning on the basis of artificial intelligence, anti-fraud platforms and services use huge amounts of data, applying methods of machine learning, statistical and behavioral analysis. This combination allows defense systems to have high capabilities to detect and stop fraudulent activities, including bots of varying complexity. By applying sophisticated algorithms and dynamic tools to detect fraudulent attribution, anti-fraud platforms prevent fraud attempts at the device, publisher and media source levels both in real-time and after attribution.
Real-time blocking
A critical component of fraud protection systems to protect advertisers from fraudulent activity in real time. When a fraudulent install is detected, its attribution is immediately blocked, preventing further engagement and attribution of any subsequent internal events from the same user. Data on blocked installations and internal events is documented in reports specifically designed to track fraudulent activity.
While the goal is to block as many ad frauds as possible in real time, it is important to strike a balance to avoid over-blocking. Excessive blocking can damage publisher relationships, ad network revenue, and data accuracy. Defense systems should be carefully tuned to strike the right balance between blocking fraud and maintaining healthy ad partnerships.
Post-attribution fraud detection
Unlike fraud that is blocked in real-time, post-attribution fraud is detected and processed retrospectively, allowing for deeper analysis of patterns and behavior over a period of time.
Fraud protection systems, such as AppsFlyer’s Protect360, utilize sophisticated algorithms and data analytics to detect post-attribution fraud. These systems continuously monitor installations and internal application events for several days (up to 8) after attribution. Once a sufficient amount of fraudulent activity is identified and a pattern is established, subsequent installations with a similar pattern are immediately recognized as fraudulent.
Basic Fraud Techniques and Measures to Combat Them

☑ DeviceID reset fraud
Fraudsters: continually reset DeviceID on the same device to generate a large number of fraudulent installations.
Fraud Software: detects an abnormal number of new devices and places their supply sources on the banned list accordingly.
☑ Customization hijacking
Fraudsters: embed malware on mobile devices that sends a notification when an app is downloaded. They intercept click attribution and claim undeserved credit.
Fraud Software: blocks attributed clicks with a very short CTIT defined by server-side APIs such as the Google Play API, for example.
☑ Clickjacking
Fraudsters: malware identifies a click on an installation attribution link and instantly sends another click, which is favored if it is attributed.
Fraud Software: blocks attributed clicks that occur a very short time after other clicks on the same device and application.
☑ Click Flooding
Fraudsters: send out large numbers of fake clicks to ensure the last click before installation.
Fraud Software: blocks clicks received using site IDs with low conversion rates and long CTIT.
☑ Behavioral Anomalies
Fraudsters: perform inconsistent and unusual actions after installation to fool fraud protection systems.
Fraud Software: detects “non-human” behavior in near real-time and blocks it at the source. Behaviors are tracked and recognized at multiple levels such as application, region, media source, and publisher.
☑ Denied IP address lists
Fraudsters: use click farms that can be identified by their IP addresses over time.
Fraud Software: IP addresses suspected of being involved in fraud are blacklisted daily based on the most recent data from a third-party provider. Fraud defense systems use IP address blacklists to prevent fraudulent traffic.
☑ SDK authentication
Fraudsters: send fake SDK messages to mimic the actions of valuable users.
Fraud Software: fraud protection system uses a proprietary hashing protocol to encrypt messages between SDKs and web services, providing protection against spoofed messages.
☑ Store verification
Fraudsters: send fake SDK messages to simulate in-app installs or in-app purchases, allowing them to demand high fees per action (CPA).
Fraud Software: fraud protection uses installation verification for iTunes and in-app verification for iTunes and Google Play to ensure legitimate installations and in-app purchases, preventing fraudulent attribution.
The issue of fraud is indeed extremely relevant in in-app advertising. Unscrupulous publishers continuously develop new ways to circumvent anti-fraud systems. Classic MMP anti-fraud tools like Appsflyer’s Protect360 and built-in fraud prevention tools like Adjust, unfortunately, do not always timely incorporate solutions to detect new types of fraudulent traffic.
This situation occurred this year with the rise of SDK fraud, which is still not detected by, for example, the widely used anti-fraud system Protect360. Such traffic appears completely “clean”; classic fraud metrics are within normal ranges, and anti-fraud tools label it as genuine, non-fraudulent traffic. However, in reality, the intended actions are simulated, and no real revenue is generated for clients. This type of fraud is often found in a significant quantity in CPA (Cost Per Action) offers, typically on Android.
The most effective approach to prevent such traffic is to use a CRM system as a verification tool. We recommend that our clients pay attention to the proper setup of the CRM system and its integration with MMP. In the vast majority of cases, such a partnership system helps protect against SDK fraud and prevents the wastage of the advertising budget on fake traffic that does not generate real revenue.
Alexandr Igonin, Affiliate Team Lead, Mobio Group
All participants of advertising interaction suffer from low-quality traffic and fraudulent actions, so the need for anti-fraud systems is obvious. And although fraud protection requires some investment, such services, both standalone and embedded, have powerful tools to fight attackers. To help you better navigate and choose the right service for you, in the next article Mobio Group will provide an overview and detailed analysis of the leading anti-fraud systems.